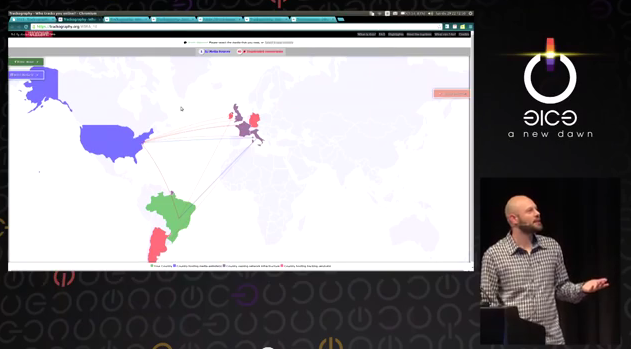
We officially launched our new project, Trackography, at the Chaos Communication Congress in Hamburg in December. Find out where your data goes, and through which countries and companies, when you read your favourite newspapers online.
In the Loop comes out every month. Catch up on what we've been up to at Tactical Tech, find out about launches and events, and look through some of the more interesting things we've found on the internet this month (culled from our Twitter feed).

We officially launched our new project, Trackography, at the Chaos Communication Congress in Hamburg in December. Find out where your data goes, and through which countries and companies, when you read your favourite newspapers online.

The books have arrived from the printers, complete with new layout and a new cover!
Watch our official unpacking video, "The Arrival".
See how the new cover was made, in this post by the designers.
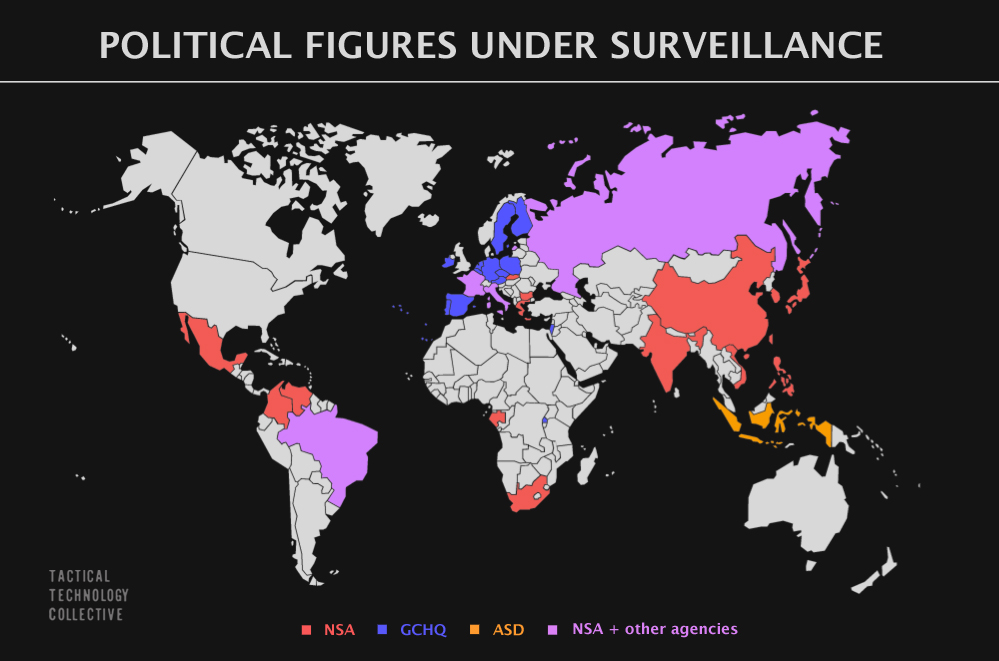
Part 3 of our Snowden-inspired blog series on myshadow.org challenges the notion that mass surveillance allows individuals to “hide within the crowd". Part 4, "Lies and Revelations" looks at why mass surveillance is not about catching the "bad guys".

(Image: Ali Ferzat)
It is unusual for Tactical Tech to comment on a current political event; however, the attack on the artists and journalists working for the French magazine Charlie Hebdo has particular significance for our work. Some initial thoughts here.
"Enabling encryption in communication services doesn't change this business model nor does it necessarily protect all of your data. So what does end-to-end encryption in WhatsApp mean?" Find out more on MyShadow.
Tactical Tech's Becky Kazansky looks at privacy enhancing technologies and human rights in the Internet Policy Review journal on internet regulation.
Tactical Tech's Kaustubh Srikanth investigates how the Indian Govt has been blocking websites, and what can be done do to get around it. (Huffington Post)

Our Exposing the Invisible film series will be closing the Creative Commons film festival in Madrid on Feb 01. Director Marek Tuszynski will be there too!

Our director Stephanie Hankey talked visualisation for advocacy with Art Review (vol 66 no 9), alongside designer and theorist Mushon Zer-Aviv and 'Beautiful Evidence' author Edward Tufte. Read the piece in the print edition.
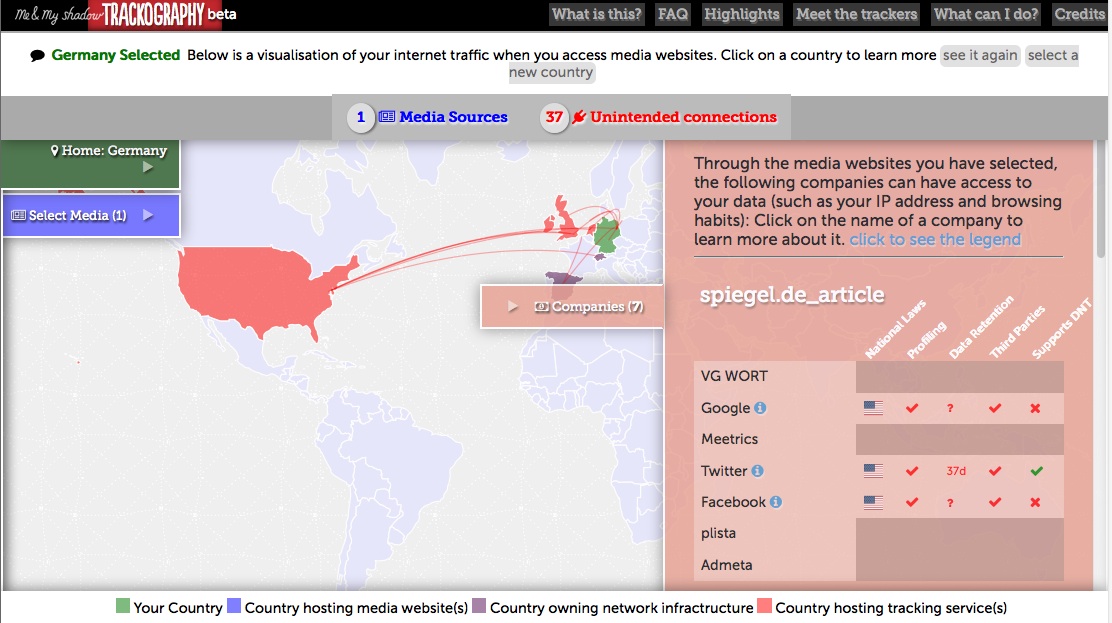
Read more about the project in Netzpolitik (in German), Annedotica Magazine, and Tech the Future.

A new article about Berlin as a centre for alternative digital activity is out, this time in "D", the weekend magazine of Italian newspaper La Republica. (17.01.2015, print edition)

Read more about our guide for environmental rights defenders in sub-Saharan Africa (Land Coalition blog).

Pussy Riot were awarded the Hannah Arendt prize for political thinking, for activism on behalf of prisoners. (Deutsche Welle)

Image: Christoph Wachter & Mathias Jud, Can You Hear Me, 2014.
....What would you say? A mesh network installation in Berlin makes this a real question.

Deep Lab member Ingrid Burrington. Screenshot: Deep Lab.
An all-women hacker collective is making art about the Post-Snowden Age.
A member of the Swedish Pirate Party set up an open Wi-Fi network at the Society and Defence National Conference, collecting and analyzing the metadata of those who connected to it.
"Someone stole naked pictures of me. This is what I did about it". Danish journalist Emma Holten in The Guardian.
"What the Charlie Hebdo attacks reveal about our thorny relationship with Satire" (Salon)
"The Limits of Satire", by Tim Parks (New York Review of Books)
"Unmournable bodies", by Teju Cole (New Yorker)
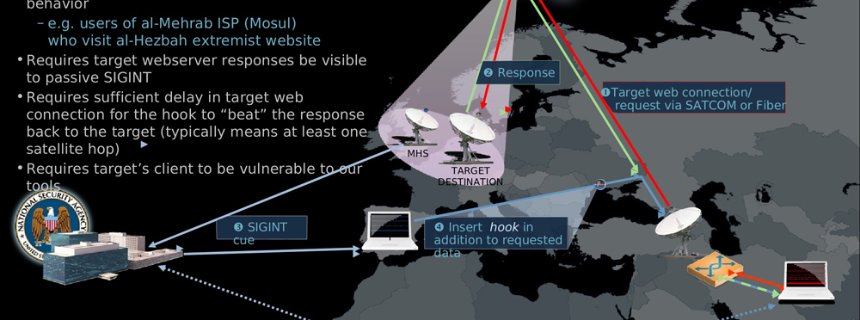
The digital arms race: NSA preps America for future battle (der Spiegel)
GCHQ captured emails of journalists from top international media (The Guardian)
"Online harassment is a digital rights issue. At its worst, it causes real and lasting harms to its targets, a fact that must be central to any discussion of harassment." (Electronic Frontier Foundation)
Also read: "Twitter's policies explicitly ban violent harassment. But it ignores vile rape and death threats. What gives?" (Salon)
"What David Cameron just proposed would endanger every Briton and destroy the IT industry" (Cory Doctorow, Boingboing)

Image: Mediengruppe Bitnik
"It turns out the police are just as happy to seize algorithmically-bought drugs, too." (Vice)
"No matter how tightly you hold your secrets, Google probably knows." (Washington Post)
Also read: How Google knows what you want to know (Medium.com)
Algorithms: "Those strange numerical gods who decide whether or not you’re a terrorist and what kids’ toy is going to set the market on fire this Christmas. But what are they, where did they come from and how did they get so powerful? " (Adbusters magazine)
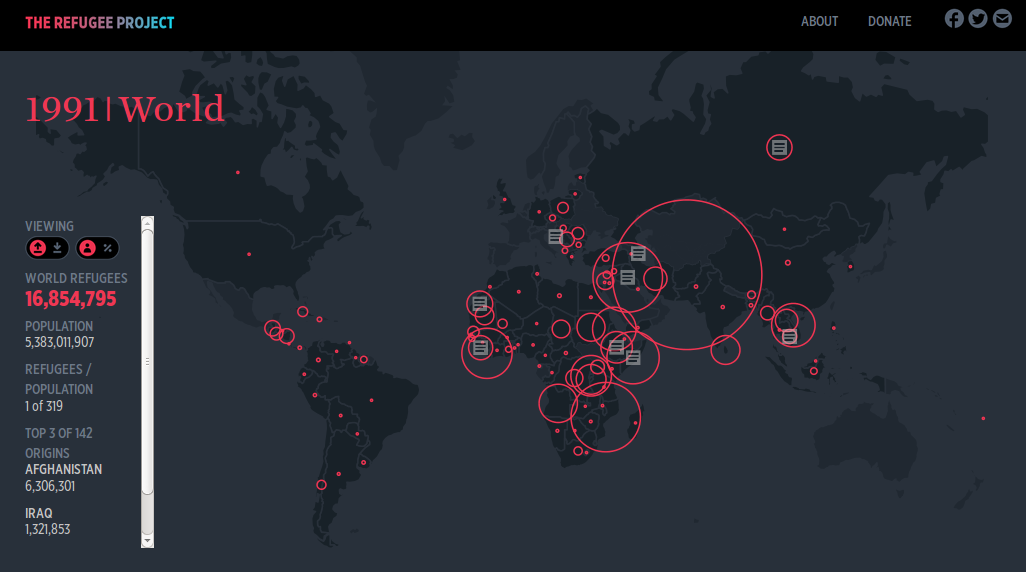
(Screenshot: the refugee project)
Interactive map of refugee migrations around the world in each year since 1975.